
A data breach can have severe consequences for your business. Not only can it lead to loss of customer trust and financial damages, but it can also damage your company’s reputation. Most businesses invest in a premium website scanner and other security measures to prevent themselves from becoming the next data breach victim. However, even though they are highly effective, you need to be aware of the different types of data breaches so you can be prepared if one occurs.
This article will discuss the most common types of data breaches and how they can affect your business.
Hacking
Sometimes, unauthorized individuals gain access to your company’s systems and data. Hacking can be done through various means, such as using malware or brute force attacks. Hackers are usually motivated by either financial gain or a desire to cause damage. If your systems are breached, the hackers could access sensitive information, such as customer credit card details or personal data. This could lead to identity theft, financial losses, and reputational damage for your business.
Phishing
Phishing is a type of cyberattack involving hackers posing as a trusted entity to trick victims into revealing sensitive information. This is usually done through email, but it can also be done over the phone or through social media. Hackers use phishing attacks to steal login credentials, financial information, and other sensitive data. They can then use this information to commit fraud or sell it on the dark web.
Phishing attacks can have a serious impact on businesses. They can lead to data breaches, financial losses, and damage to reputation. To protect your business from phishing attacks, you should educate your employees about how to spot them and have a strong cyber security policy in place. You should also consider using a spam filter or email encryption service.
Ransomware
This type of attack is becoming increasingly common. In a ransomware attack, hackers gain access to your systems and encrypt your data. They demand a ransom to decrypt the data and return it to you. This type of attack can be devastating for businesses, as it can lead to the loss of important data and disruption to operations.
Ransomware attacks can have a devastating effect on businesses. They can lead to data loss, financial losses, and damage to reputation.
To protect your business from ransomware attacks, you should have a strong cyber security policy in place. You should also consider using a backup service so that you can restore your files if they are encrypted.
Malware
Malware is a type of malicious software that is designed to damage or disable computers. It can be used to steal information, hijack systems, or encrypt data so it can’t be accessed. If your business’s systems are infected with malware, it can cause disruptions in service, data loss, and financial damage. You may also be at risk of legal action if sensitive data is leaked or stolen.
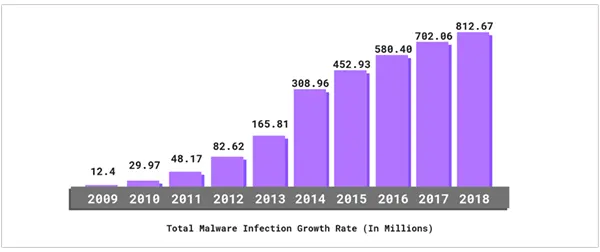
This bar graph shows the constant rise in total number of Malware Infection Growth Rate (in millions) from the year 2009 to 2018.
Insider Threats
An insider threat occurs when a current or former employee, contractor, or vendor steals information or sabotages your business. This can be done deliberately or accidentally. The most common type of insider threat is when an employee steals information for personal gain. This could be something as simple as taking customer data to sell to a competitor, or it could be more malicious, like planting malware on your systems.
Accidental insider threats are usually the result of employees not following best practices or not understanding how their actions can affect your data. For example, an employee might accidentally click on a phishing email and give attackers access to your systems, or they might connect their work laptop to an unsecured Wi-Fi network and expose sensitive data.
Preventing insider threats starts with educating your employees about cyber security and having strict policies in place. You should also consider using security tools like data loss prevention (DLP) software to monitor employee activity and prevent leaks of sensitive data.







