Also known as a pen test, penetration testing is a simulated cyber attack against a computer system. This report is used to identify exploitable flaws. In the context of web application security, it is used to complement a web application firewall (WAF).
One could say that penetration testing is a core element of an organization’s cyber attack defense since it helps in detecting vulnerabilities that are exploitable by an attacker.
Vulnerabilities may occur due to reasons like misconfiguration, insecure code, inadequately designed architecture, or disclosure of sensitive information.
Nevertheless, it is not the mere identification of these vulnerabilities that makes penetration testing truly valuable but reports showing concrete steps to address them.
A good penetration testing report can act as a map for making an organization’s posture stronger from a security point of view.
This guide discusses what are the major elements and proper recommendations for writing a penetration testing report.
Methodology
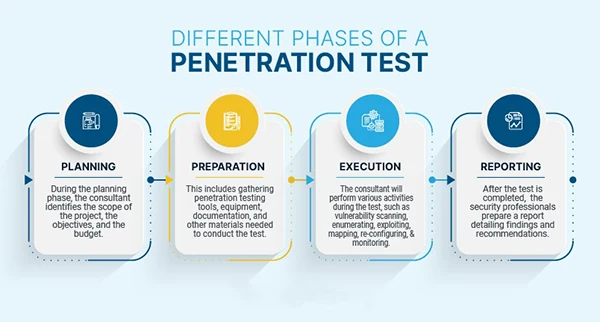
Penetration testing methodology is a specific course of action. It is typically taken by the pentest provider to conduct the pentest of a target website or network.
Right now, there are multiple penetration testing methodologies to choose from. When deciding to use penetration testing, the decision must be based on the target business, the goal of the pentest, and its scope.
Do You Know?:
As per recent studies, worldwide cybercrime costs are estimated to hit $10.5 trillion annually by 2025. The growing numbers emphasize the need for enhanced cybersecurity measures.
Discuss the methodology used during the penetration test, types of tests performed (black box vs. white box vs. gray box), tools and techniques utilized, as well as the boundaries of this assessment.
This segment provides the background to the findings and confirms that the testing process was exhaustive.
However, penetration testing methodologies are as follows:
- Data collection: Target system data can be collected via Google search and Web page source code analysis. Using these techniques, you can collect information about the system, software, and plugin versions.
Also, with an array of tools (like Acunetix, Aircrack-ng, Cain & Abel, Ettercap, John the Ripper, Metasploit, Nessus, Kismet, and Wireshark), acquire information like database, table names, software versions, and hardware used by various third-party plugins.
- Vulnerability Assessment: Security weaknesses can be identified with ease. Ultimately, this will help testers to launch attacks using identified entry points in the system.
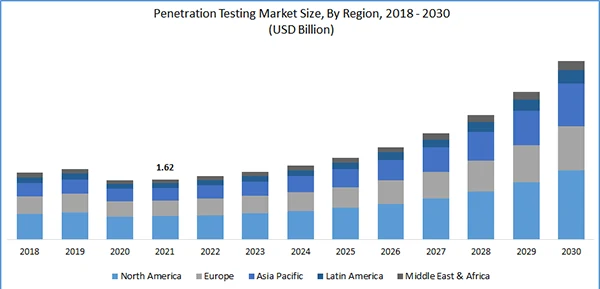
Statistics:
According to the Polaris Market Research analysis, the global penetration testing market was valued at USD 1.62 billion in 2021. Shortly, it is expected to grow at a CAGR of 13.9% during the forecast period.
- Actual Exploit: It is time to launch an attack on the target system which requires special skills and techniques. This is achievable with the help of experienced penetration testers.
- Result analysis and report preparation: Detailed reports are prepared for further corrective actions. Vulnerabilities and recommended corrective methods are noted in these reports.
You can even customize vulnerability report formats in HTML, XML, MS Word, or PDF according to different organization needs.
Findings and Vulnerabilities
Describe each vulnerability identified during the test, separated by level of importance. For each vulnerability, include the following information:
- Description: A detailed description of the vulnerability.
- Location: Where in the system or application the vulnerability was found.
- Evidence: Screenshots, logs, or other evidence to support the finding.
- Impact Analysis: An evaluation of the effect on the organization should vulnerability become exploited.
- Risk Rating: Prioritize vulnerabilities with a standardized risk rating (e.g., High, Medium, Low).
Recommendations
For each of the identified vulnerabilities, provide specific and practical recommendations on how to address them. The recommendations should be realistic and attainable based on the operations and business limitations of the organization.
If practical, recommend other mitigations if immediate fixes cannot be carried out.
Practices for Penetration Testing Reports
- Clarity and Conciseness: Make sure the report is easy to understand by both technical and non-technical readers. Define the scope of the penetration test in a way that satisfies your client and avoids ethical and legal issues.
This is noteworthy because, if esters do something outside the agreed-upon scope, they may incur legal liability.
- Customization: Customize the report to meet specific organizational needs and context. Avoid generic findings and recommendations.
- Know the Architecture: Do not forget to comprehend how the system works, how it collects and manages data in the background.
Moreover, before getting started with the test stress upon knowing how it interacts with other services and handles user requests.
- Actionability: Concentrate on delivering tangible insights that can lead to impactful security improvements.
- Document Methods: You must agree on the fact that each penetration tester has a different methodology. So, in this case, it is best to share the methods with the report’s consumers.
Each and every piece of information has been mentioned in the report because it may potentially enhance the credibility and significance of the findings.
Fast Fact:
73% of successful hacks in the corporate sector were done by getting into web applications through their vulnerabilities.
For example, testers must be asked how the team conducted reconnaissance. Have testers utilized a particular framework, such as NIST or SANS? and Why did testers attempt this particular assault and not others?
- Note Positives As Well As Negatives: Despite focusing the report on the organization’s security flaws.
If there are areas that have been secured enough or if an attempt to attack has been blocked by security measures, it is significant to document this information to enable the organization to assess the effectiveness of its defenses.
- Prioritization: Point out the most important vulnerabilities and remediation to help prioritize actions.
- Follow-Up: Suggest that there should be a second penetration test to ensure the vulnerabilities have been successfully fixed and to uncover any new problems.
Conclusion
A good penetration testing report does more than just enumerate vulnerabilities—it details a focused, tactical roadmap for strengthening an organization’s security profile.
By implementing this guide’s structure and best practices, as well as using the services of experienced professionals such as those at DigitalXraid, organizations can achieve security improvements from their penetration testing efforts.