Introduction
The world of today has a keen desire to go digital. Be it mobile phones or daily facilities everyone needs to work efficiently, fluently, quickly, and digitally.
Similar was the case when the question of currency came.
Some people believed that the sole authority of economic power shouldn’t be in the hands of moneymakers in the form of banknotes and minted coins.
As a result, the existence of Bitcoin came into being.
Somewhere in Japan a programmer or something else namely Satoshi Nakamoto presented the concept of Bitcoin to the world.
Though it was the least popular thing during that period presently it is considered to be the most secure, most famous, and protected digital currency in the world.
The technology behind the secure network of Bitcoin is the blockchain and several others constantly supporting it.
Insecurities are prevalent when something is this famous just like Bitcoin.
You Should Know:
As of now, the Bitcoin price is $36,719.73, up 2.06% in the last 24 hours, and the live market cap is $717,720,415,692.798.
In this article, we are going to shed some light on these issues that are targeting the popularity and ease of Bitcoin trading solutions.
Attacks and Their Types
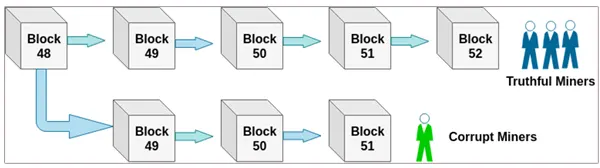
Sybil’s Attack
The blockchain that supports bitcoin trading depends on a peer-to-peer network and this type of attack has its place in this P2P network itself, thereby acting to be several identical hosts thus creating a doubtful network to work on.
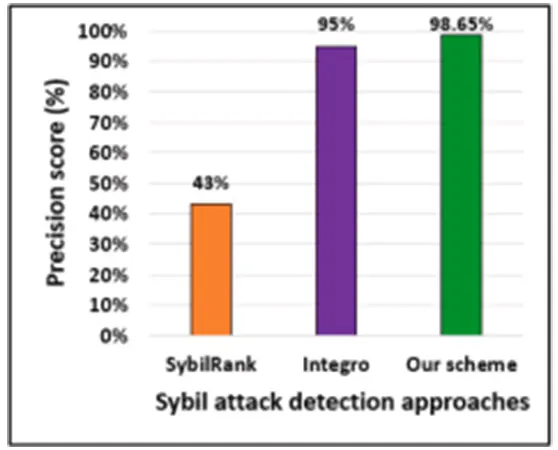
The graph is all about user behavior-based and graph-based hybrid approaches for the detection of Sybil Attacks in online social networks.
This finally results in acquiring access to the identities and thus exploiting them too large.
The attack is malicious and is considered to be the most difficult attack as far as detecting and preventing is involved.
The word Sybil itself is derived from the case study of a woman who had an identity disorder and thus is considered an identity attack sometimes.
Race Attack
There is a well-known proverb that if you can’t win over them, confuse them! A similar thing happens with this attack.
The attacker creates a conflicting transaction of the same details such as amount and date.
To make it easy, a race attack is a kind of malicious activity when two transactions are created at the same time using the same funds to spend them twice.
The approval is basically from the receiver to make the payment so when the receiver authorizes the transaction in the first next second he receives another same-looking transaction to authorize again.
If not looked at properly one can easily lend his hard-earned money online to the hands of scammers and fraudsters.
The duplication hits hard online and one should wait for his first transaction confirmation before repeating the transaction.
It is easier to carry out a race attack at times when the attacker has a direct connection to the victim’s node. And, deposits the conflicting transaction directly to the miners.
Finney Attack
This is another type of attack but is considered somewhat difficult to execute. In this type of attack, the assumption of the attacker being a miner is made.
The miner is the attacker and thus is difficult to execute. The name of the attack is derived from Hal Finney.
Interesting Fact:
The key point in this type of pre-mining attack is that they are not carried out at an “arbitrary” moment in time, but rather at a moment selected by the attacker.
Even, the Finney hack or attack is a type of hack or double spend attack.
In this attack, the coins are routed back to the miner aka attacker without letting others know about it.
The pre-mined block is used for the purpose and the same coins make rounds again and again thereby creating a fake transaction report.
Vector76 Attack
The mixture or hybrid of Race and Finney came to be known by the name of Vector76 attack.
The attacker manages to create two nodes connected to the exchange and blockchain network simultaneously.
It involves the reversal of the transaction. Low-value transactions are authorized, and high values are rejected.
The incoming connections should be checked and only those connections should be allowed that are well-connected.
The proper knowledge of attacks and methods to avert them are necessities to keep himself away from such attacks.
Experience matters and security matters the most as far as the question of currency is concerned.








