As we’ve navigated into the digital age, our daily lives have been reshaped — how we chat, share, and connect with the world. This new digital playground is teeming with opportunities but also holds hidden traps where digital predators lurk.
In the digital jungle, cunning hackers are ready to deploy sophisticated techniques like phishing, malware, and account takeovers. Hence, understanding how to secure your online presence is vital. It ensures your digital journey remains both safe and enjoyable.
Lessons on Dodging Digital Snares
To protect yourself online, you must delve into the playbook of digital tricksters, understand their tactics, and shield yourself from social media assaults.
Hook, Line, and Sinker: Phishing Explained
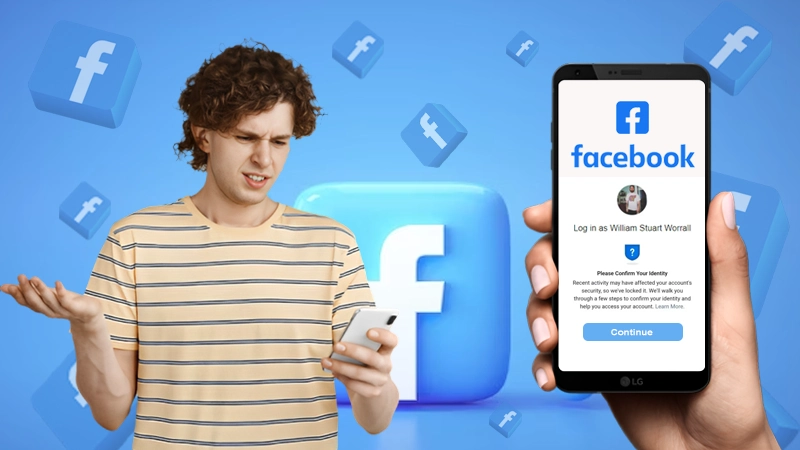
Phishing is a prevalent technique used by hackers. You might receive a legitimate email, but it’s a ploy to obtain your personal info, like usernames, passwords, and credit card details.
Phishing can often be more sophisticated than just suspicious emails. Sometimes it’s a message from a trusted friend, a notification from your bank, or even an enticing offer from a popular online store.
Malware Menaces: The Silent Invaders
Then there’s malware, destructive bits of software like viruses, worms, ransomware, and spyware that cyber crooks use to infect your devices, interfere with your data, or even take control of your device.
Digital Doppelgängers: When Your Account Gets Hijacked
Imagine a stranger impersonating you. That’s what account hijacking feels like. Hackers take over your social media account and use your digital identity; they can cause all kinds of havoc.
Mirror Image: Cloning Accounts
Cloning is another common tactic. Hackers duplicate your social media profile and reach out to your friends, launching further attacks and causing chaos in your digital community.
Building Your Digital Fortress – A Guide to Security
The digital world isn’t all gloom and doom. Here are some protective measures you can implement to keep your digital identity safe and secure.
The Might of Your Secret Code: Password Power
Your first shield against these digital foes is a strong, unique password that would baffle any hacker trying to guess it. Mix it up with uppercase and lowercase letters, numbers, and symbols.
The Dynamic Duo: Two-Factor Authentication
Two-factor authentication, or 2FA, is your following line of defense. Even if a hacker manages to crack your password, they must get past this second hurdle, which often involves a physical token or a one-time password sent to your phone.
In today’s security landscape, 2FA is becoming increasingly mandatory. It’s not just about receiving a text message with a code but also about biometrics like fingerprints, face recognition, or physical keys. Adding an extra layer of authentication significantly reduces the risk of an account breach and puts you one step ahead of attackers.
Red Flags: Spotting Suspicious Links and Messages
Digital tricksters often use links and messages as bait. They might seem harmless but can lead to dangerous websites built to steal your info or infect your system with malware. Be cautious about clicking links, especially from unknown sources or messages that seem odd coming from someone you know.
Stay Alert: Login Notifications and Session Reviews
Many social media platforms have features like login alerts and active session reviews. These let you know when your account is accessed from a new device or location, helping you spot any strange activity.
Harnessing Tech Tools for Protection
Numerous technical tools can significantly improve online security and protect your data from cyber threats.
VPN to the Rescue: Secure Connections
A VPN, or Virtual Private Network, works like your own digital tunnel. A reliable VPN paves an effective way to establish robust threat protection for your online identity and devices. It provides a secure and encrypted connection, shielding your online activities from prying eyes and making it challenging for hackers to intercept your data.
Stay Fresh: Keep Your Devices and Apps Updated
Keep your devices and apps updated. Updates often patch security holes, providing better protection against the latest threats.
Safe Surfing: HTTPS and Incognito Mode
When you’re online, make sure you’re browsing safely. Look for “https://” in the web address – the ‘s’ means ‘secure’ and indicates the site uses encryption to protect your info. Also, consider using Incognito or Private mode in your browser to keep your browsing history, cookies, and form data private.
Inside the Mind of a Hacker
To effectively shield yourself from cyber attacks, you need to understand the tactics and tools of the criminals, the manipulative art of social engineering, and the potential fallout of data breaches.
Criminal Masterminds and Their Tech Arsenal
Today’s hackers aren’t lone wolves but are often part of organized rings equipped with advanced hacking tools. They exploit even the smallest weaknesses in your digital defense, often using software bought from the internet’s darkest corners.
These cybercriminals continuously learn, evolve, and find new ways to invade your digital life. They take advantage of the ever-expanding technological landscape and exploit emerging technologies like Artificial Intelligence and machine learning to carry out sophisticated attacks. The dark web often serves as their marketplace, where they buy and sell illicit tools, services, and even stolen data.
Mind Games: The Art of Social Engineering
Hackers exploit human trust through social engineering. They manipulate people into revealing sensitive info, impersonating someone you trust, or creating a fake crisis that prompts you to act.
The Aftermath: Data Breaches
When a cyber-attack succeeds, the aftermath can be a nightmare. Personal and financial information might be exposed, causing harm to the victims that go beyond financial loss.
Good Cyber Habits 101
Good old habits are key to a safe digital life. Here are some easy-to-follow steps to improve your cybersecurity routine.
Knowledge is Power: Stay Informed and Spread the Word
Staying vigilant and up-to-date is key to securing your online presence. Follow reliable sources for the latest threats and safety measures, and share this with your friends and family.
Keep an Eye on Your Digital Footprint
Regularly check your social media accounts for anything odd. Unusual posts, friend requests, or messages could indicate a breach.
Back-Up Your Data Safety Net
Keep a backup of your important data. It’s your safety net in case of a malware attack or data breach. Creating regular backups should be an integral part of your digital routine.
Remember, it’s not just about backing up your device locally but also about considering cloud solutions, which provide a remote safety net. Encryption should also be used to secure these backups. In a data loss incident, backups allow you to restore your information without significant downtime or expense.
Have a Plan: Your Cybersecurity Emergency Protocol
Having an emergency plan ready in case of a cyber threat is crucial. It should include who to contact, steps to isolate the compromised device or account, and actions to limit the damage.
Dealing with the Worst: Compromised Accounts
Despite all precautions, there might be times when your account gets compromised. Here’s how to manage such situations and bounce back from an account breach.
Take Immediate Action: Regain Control
If you think your social media account’s been hacked, act fast. Try to regain control by changing your password, reporting the breach to the platform, and alerting your contacts to ignore any strange messages from your account.
Bounce Back: Recover and Prevent Future Breaches
Once you’re back in control, review your account settings and activity to undo any changes made by the hacker.
Be Cyber Smart
Being a responsible social media user means prioritizing online safety. Understanding the threats, implementing security measures, and practicing good cyber habits can keep you safe online.
The fight against cyber threats is collective, and every step you take toward securing your digital life contributes to the broader goal of creating a safer online world for everyone.