Zero-Trust Security is a game-changing cybersecurity technique that has gained traction in today’s digital world. This method calls into question the typical assumption of trust in network settings, assessing each access request as a possible threat.
Read on and look into the fundamental concepts of Zero-Trust Security with its inherent advantages. This article will also delve into the major challenges businesses may encounter while implementing this innovative approach.
What Exactly Is Zero Trust Security?
Zero trust is for prevention, which implies no entity, including the organization, can be trusted entirely. It is an open-minded approach to cybersecurity, in which every encounter is seen as a possible danger that requires rigorous investigation and risk assessment.
This model considers the complete network and all linked devices, which means that authentication, authorization, and other protective standards are applied. It is necessary to utilize it on every device, user, and piece of data that interacts with the connection.
This all-encompassing strategy allows firms to recognize and react to threats rapidly, making it impossible for attackers to go undiscovered for long periods.
It also guarantees that authorized devices and users are subject to safety procedures, prohibiting authorized devices from bypassing protective measures.
DO YOU KNOW?
The term Zero Trust was coined by Stephen Paul Marsh in 1994, and popularized by security analyst John Kindervag. Google was one of the first tech companies to try a form of zero-trust security in 2009.
The Three Concepts of Zero-Trust
Today, the zero-trust model is implemented in a variety of ways, including zero-trust network access (ZTNA), zero-trust architecture (ZTA), and zero-trust edge (ZTE). They are, nevertheless, all based on the same fundamental ideas.
Three zero-trust concepts guide the approach:
Assume That Every Network Traffic Is a Risk at All Times
Zero trust holds that every user is hostile and that dangers exist within and outside the network. As a result, any traffic that does not have express authorization is refused access.
Every device, user, and connection flow is verified, approved, and confirmed continuously when seeking admission.
Enforce Least-Privileged Access
Zero trust techniques give the least privileged access and admission to the resources that are required when they are needed without interfering with the ability to perform a job.
If an account or device is hacked, the least privileged avenue prevents attackers from migrating laterally to more vital assets.
Monitor Always
The zero-trust concept suggests continuous monitoring and constantly examines and monitors network activities. This allows for real-time awareness of which entities are attempting to enter resources.
It also aids in identifying possible threats, current occurrences, and anomalies that should be examined.
What Are the Main Advantages of Zero-Trust Security?
The following are the main advantages of the zero trust security approach.
Increased Visibility
The implementation of zero trust requires companies to be aware of the whereabouts of their assets. They continually monitor the identities of those who admit resources and how they do so.
The visibility and context of traffic, asset inventory, and risk management are all improved.
Access Control in Modern IT Environments
Safety rules are developed based on the user’s identification and tied to individual workloads using a zero-trust architecture.
This places protection close to the assets being safeguarded and enables it to move along with the workload regardless of where it is being performed.
Consistent Compliance
Under the zero trust model, every bit of traffic and request is recorded and scrutinized. In addition to this, it restricts entry to the available assets.
This not only makes it simpler to verify that you have done all in your power to comply with data privacy regulations and standards, but it also makes it possible to create a clear audit trail if a breach occurs.
Consistent and Adaptable Security
Regarding security, policies are centralized and controlled in zero-trust models, and automation is relied on to migrate and update rules based on context.
In addition to making these preventive measures more adaptable and scalable, this reduces the workload placed on system administrators.
Reduced Attack Surface and Risk
Zero trust separates traffic and establishes network segments to avoid lateral movement and spreading dangerous diseases to relevant resources.
Any suspect behavior may be investigated and identities re-verified using rules and controls, reducing the likelihood of a successful breach.
Limit the Breach’s Blast Radius
Zero trust helps to restrict the breadth of harm if and when a breach occurs since identities are granted least-privilege admission.
This allows teams to react to and neutralize attacks more quickly, reducing the danger of future exposure.
The aftereffects of the pandemic promoted a hybrid work culture, which also opened channels of communication regarding increased cybersecurity measures. Although VPN is considered relatively safer than local network service providers, companies like Microsoft realized greater risk threats.
The graph below shows that zero trust is required to be implemented in all network areas on all devices for robust security.
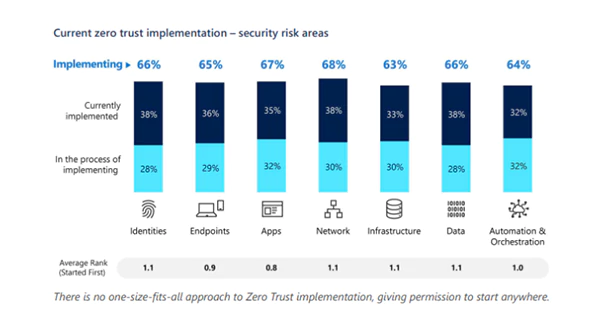
The Challenges of Using the Zero-Trust Model
Of course, every approach has challenges. Making the transition to zero trust takes time and needs careful preparation.
Here are some of the most significant challenges of using zero trust:
Inhibiting Productivity
When done improperly, zero trust adds unnecessary preventive stages to most activities and may reduce productivity. The idea is to strike a strategic balance between enabling work and having a robust safety posture. Individuals may strive to avoid procedures if they become too disruptive.
Defending Against Insider Threats
While zero trust may assist in mitigating insider risks via least-privilege access, it is not a panacea. Attackers usually discover methods to get entry by stealing credentials and tricking users into revealing sensitive information via phishing or scareware.
In the worst-case scenario, you may deal with an unethical actor looking to misuse their powers. Zero trust must be able to monitor and identify any pattern irregularities throughout the business to succeed against insider threats.
Being Consistent
When done correctly, zero trust may provide better protective measures. However, it also necessitates that firms adhere to their plan.
Most businesses will need to make gradual adjustments as they transition away from old safety solutions, but they must also guarantee that no holes arise along the way.
Keeping Policies and Architecture
Because your company is constantly expanding and developing, your zero-trust rules and authorization structures must also be updated regularly.
Zero-trust models depend on well-defined regulations and good policy administration, which must be continually maintained and set to avoid breaches.
Conclusion
In an age of ever-changing dangers to cybersecurity, zero-trust security is an effective way of safeguarding corporate assets. Organizations may strengthen their defenses against internal and external threats by adopting mistrust principles, instituting tight access controls, and encouraging continual monitoring.
This transformation, however, is manageable, as it needs precise preparation, consistency, and flexibility to reach the full potential of the zero-trust paradigm. Nonetheless, the benefits of increased protection and decreased danger are well worth the effort.






